The Anti-Phishing Working Group (APWG) has just released its Phishing Activity Trend Report for Q1 2021.
The first findings are easily predictable; the dispersion of the workforce is pushing phishing attacks to new records: just in January 2021, the APWG detected 245,771 unique phishing sites, the highest number reported so far.
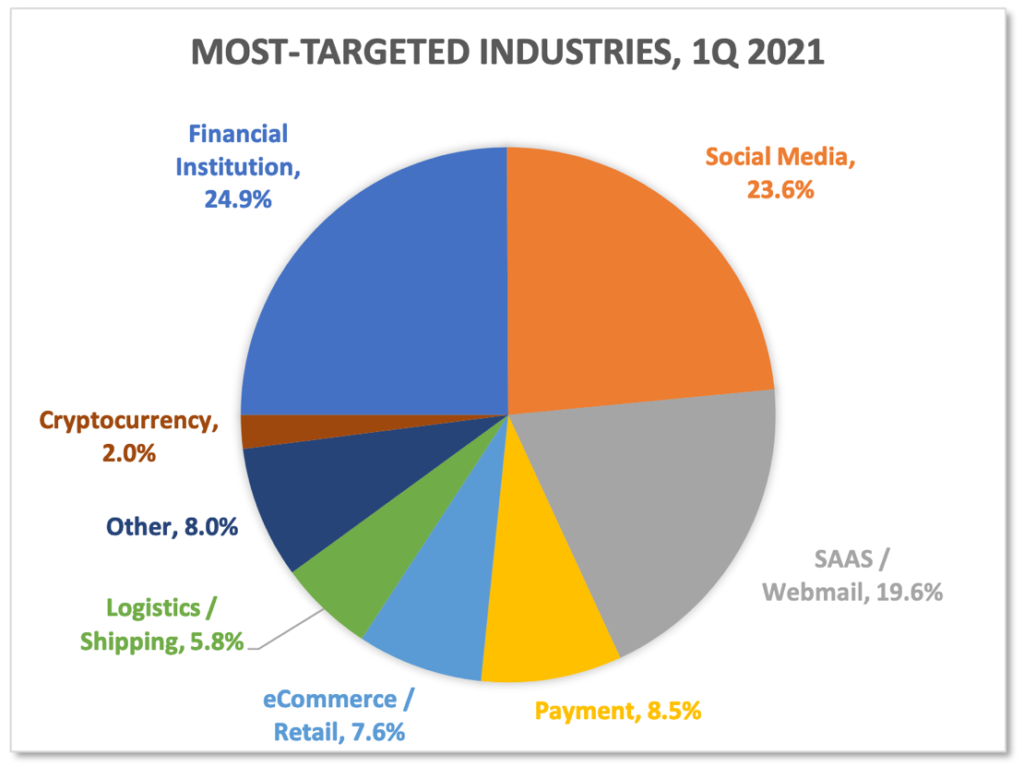
Looking at the most targeted industries, in the first quarter of 2021 phishing attacks against financial institutions were still the most prevalent (24.9% of all attacks, up from 22.5% in Q4 2020), ahead of social media, which moved into second place with 23.6% (up from 11.8% in Q4 2020), and SaaS/Webmail (19.6%, down from 22.2% in Q4 2020). SaaS/Webmail continues to be among the most targeted verticals, but what is really noticeable is the rise of social media, a vertical which represents a threat for corporate users, considering that 83% of them have personal apps on company-managed devices.
Another interesting finding of the report is the confirmation that TLS encryption is now the norm for phishing attacks. 83% of attacks were carried out hosting the phishing page on an HTTPS site to encrypt the communication between the victim and the malicious page itself.
Finally, Business Email Compromise (BEC) continues to play an important role in the cybercriminal ecosystem. The average amount requested via wire transfer increased by 14%, from $75,000 in Q4 2020 to $85,000 in Q1 2021. What’s also interesting is the role cloud services play in this kind of attack: 7.8% of the domains used by BEC scammers were hosted on Google, which should not be surprising considering cloud email services such as Gmail (but also Microsoft Office 365) are often exploited by BEC scammers.
How Netskope mitigates the risk of phishing
The Netskope Next Gen Secure Web Gateway, a module of the Netskope SASE platform, enforces web filtering directly from the cloud for more than 120+ categories and languages for 190+ countries covering 99.9% of the active web. Corporate users are protected on any device, regardless of where they are connecting from, and regardless of what they are accessing (whether it’s a corporate or personal cloud application or a web page). The SASE platform performs TLS decryption at scale, so full content inspection and security enforcement occurs even if the phishing site is using HTTPS. In addition, the same efficacy, and the same security controls are applied if the phishing page is delivered from a rogue instance (or a compromised instance) of a cloud service. Additionally, the Cloud Threat Exchange enables Netskope customers and technology partners to bi-directionally exchange IOCs, including URLs, that can be imported from third-parties to complement the Netskope threat intelligence.
The exploitation of a corporate cloud service to launch a BEC attack can be mitigated via the UEBA engine, one of the pillars of the CASB module available both inline and via API. The UEBA engine, powered by machine learning, can detect anomalous events on corporate-managed cloud services, such as Google Workspace or Microsoft 365, which could indicate the execution of a malicious activity.
Stay safe!




 Retour
Retour 





















 Lire le blog
Lire le blog